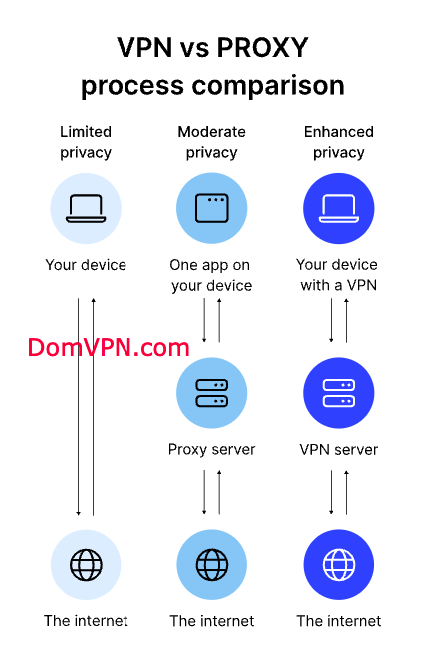
In today’s digital landscape, internet privacy and security concerns are at an all-time high. With cyber threats, data breaches, and invasive surveillance becoming increasingly common, safeguarding your online activities is more important than ever. Proxy servers and Virtual Private Networks (VPNs) are two popular tools for enhancing online privacy. But how do you determine which one is right for you? This comprehensive guide will explore the key differences between proxies and VPNs to help you make an informed decision.
1. What is a Proxy Server?
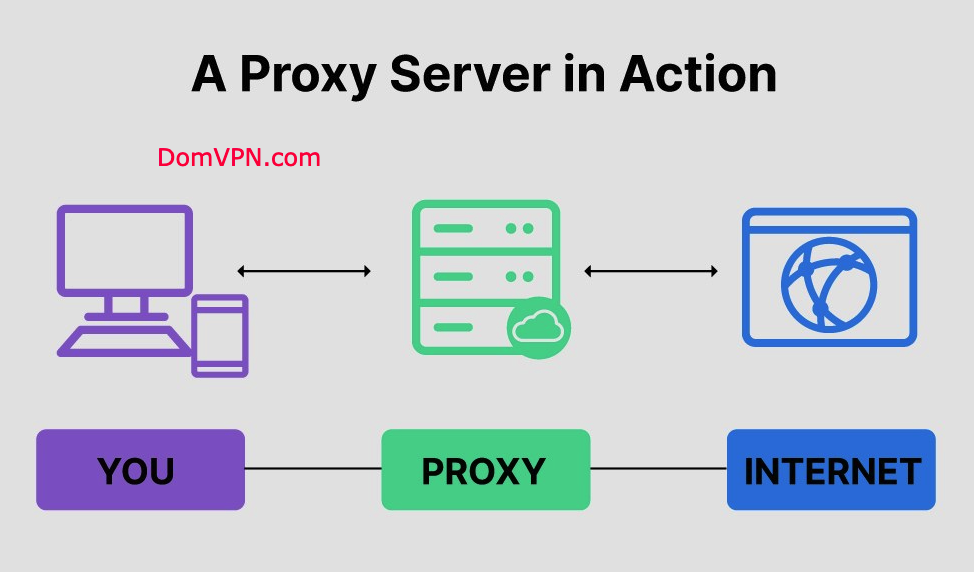
A proxy server acts as an intermediary between your device and the internet. When you connect through a proxy, your internet requests are routed through the proxy server first. This process masks your original IP address, making it appear your traffic originates from the proxy server.
Types of Proxy Servers
- HTTP Proxies: Designed specifically for web browsing and handling HTTP and HTTPS requests.
- SOCKS Proxies: Versatile proxies that handle various types of traffic, including email, file transfers, and peer-to-peer sharing.
- Transparent Proxies: Often used by organizations to monitor user activities without altering requests or providing anonymity.
Common Uses of Proxies
- Bypassing Geo-Restrictions: Accessing content that is otherwise unavailable in your region.
- Web Scraping: Collecting data from websites anonymously for analysis.
- Basic Anonymity: Hiding your IP address for simple privacy needs.
2. What is a VPN (Virtual Private Network)?
A VPN creates a secure, encrypted tunnel between your device and a VPN server. All your internet traffic passes through this tunnel, ensuring your data remains confidential and your IP address is concealed.
How VPNs Work
- Encryption: VPNs use advanced encryption protocols to secure data transmitted over the internet.
- Tunneling Protocols: They encapsulate your data packets within encrypted packets, making them unreadable to unauthorized parties.
- Server Networks: VPN providers offer a network of servers in multiple locations, allowing you to choose your virtual location.
Common Uses of VPNs
- Enhanced Privacy and Security: Protecting sensitive information from hackers and surveillance.
- Accessing Geo-Blocked Content: Streaming services or websites restricted in your country.
- Secure Remote Work: Providing employees with secure access to company networks from remote locations.
3. Key Differences Between Proxy and VPN
Privacy and Anonymity
- Encryption Levels: VPNs encrypt your internet connection, while most proxies do not offer encryption.
- IP Masking: Both proxies and VPNs hide your IP address, but VPNs provide a higher level of anonymity due to encryption.
Speed and Performance
- Internet Speed: Proxies may offer faster connections since they lack encryption overhead, but this comes at the expense of security.
- Bandwidth Considerations: VPNs may slow down your connection slightly due to the encryption process.
Security Features
- Protection Against Threats: VPNs offer robust security features, including encryption and sometimes malware protection.
- Vulnerability: Proxies lack advanced security measures, exposing you to potential threats.
Use Cases
- Proxies: Best for low-risk activities like bypassing simple content restrictions.
- VPNs: Ideal for securing sensitive data and maintaining privacy across all online activities.
4. Proxy vs VPN for Torrenting
Torrenting involves downloading and uploading files through a peer-to-peer network, which can expose your IP address to other users.
Risks Associated with Torrenting
- Legal Consequences: Downloading copyrighted material can lead to legal action.
- Security Threats: Increased exposure to malware and cyber-attacks.
Effectiveness of Proxies in P2P Sharing
- Limited Protection: While proxies can hide your IP address, they don’t encrypt your data, leaving you vulnerable.
- Not Ideal for Security: The lack of encryption makes proxies less suitable for safe torrenting.
Advantages of VPNs for Secure Torrenting
- Encryption: VPNs encrypt your data, protecting your activities from prying eyes.
- Anonymity: Concealing your IP address enhances your privacy and reduces the risk of being tracked.
5. Residential Proxy vs VPN
Explanation of Residential Proxies
Residential proxies use IP addresses assigned by Internet Service Providers (ISPs) to homeowners. This makes your connection appear to be coming from an actual residential address.
When to Choose a Residential Proxy Over a VPN
- Web Scraping: To mimic actual user behavior and avoid detection.
- Ad Verification: Ensuring that ads are displayed correctly in different locations.
Comparative Analysis
- Anonymity: Residential proxies offer a high level of anonymity but lack the security features of VPNs.
- Security: VPNs provide anonymity and encryption, securing your data from end to end.
6. Reverse Proxy vs VPN
Definition of Reverse Proxy
A reverse proxy sits in front of web servers and forwards client requests to those servers. It effectively hides the identity and characteristics of the backend servers.
Use Cases in Corporate Environments
- Load Balancing: Distributing incoming traffic across multiple servers to optimize resource use.
- Security: Protecting internal servers from direct exposure to the internet.
Comparison with VPN Functionalities
- Purpose: Reverse proxies manage and distribute incoming traffic to servers while VPNs secure client-side connections to the internet.
- Security Features: VPNs focus on encrypting data between the user and the VPN server; reverse proxies do not encrypt client-server communication.
7. SOCKS5 Proxy vs VPN
Overview of SOCKS5 Proxy Protocol
SOCKS5 protocol routes network packets between a client and server through a proxy server. It is more flexible and efficient than earlier proxy protocols.
Performance and Security Aspects
- Speed: SOCKS5 proxies are generally faster because they transfer smaller data packets.
- Security: They do not encrypt your data, leaving it vulnerable to interception.
When to Use SOCKS5 Proxy vs VPN
- SOCKS5 Proxy: Suitable for applications where speed is crucial and security is a lesser concern, such as streaming or gaming.
- VPN: Preferred when security and data encryption are essential.
8. Tor vs. VPN vs Proxy
Introduction to the Tor Network
The Tor network anonymizes your internet connection through multiple volunteer-operated servers called nodes or relays.
Security and Anonymity Comparison
- Tor: Offers high levels of anonymity but can significantly reduce browsing speed.
- VPN: Provides a balance between speed, security, and anonymity.
- Proxy: Offers basic IP masking without encryption.
Advantages and Disadvantages of Each
- Tor
- Advantages: Maximum anonymity.
- Disadvantages: Slow speeds, not ideal for streaming or downloading large files.
- VPN
- Advantages: Strong encryption, good speeds, versatile use cases.
- Disadvantages: May require a subscription fee.
- Proxy
- Advantages: Faster connections are due to the lack of encryption.
- Disadvantages: Minimal security and privacy features.
9. How to Choose Between a Proxy and a VPN
Assessing Your Privacy Needs
- Basic Privacy: A proxy might suffice if you need to hide your IP address only for simple tasks.
- Enhanced Security: A VPN is recommended to protect sensitive data and comprehensive privacy.
Evaluating Security Requirements
- Data Protection: VPNs encrypt your data, making them suitable for securing personal or financial information.
- Anonymity Needs: Consider using the Tor network in conjunction with a VPN for high-stakes anonymity.
Considering Speed and Performance
- High-Speed Requirements: If speed is a priority and security is less of a concern, a proxy may be adequate.
- Willingness to Trade Speed for Security: VPNs might slightly reduce your internet speed due to encryption but offer greater security.
Budget Considerations
- Free Options: Free proxies and VPNs are available but often have limitations such as data caps, slower speeds, and security risks.
- Paid Services: Offer better performance, enhanced security features, and customer support.
10. Frequently Asked Questions
Can I Use a Proxy and a VPN Together?
Yes, it’s possible to use both simultaneously, but it can be complicated to configure and may not provide significant benefits over using a VPN alone.
Are Free Proxies and VPNs Safe?
Free services often have drawbacks, including limited features, slower speeds, and potential privacy risks. Some may log your data or inject ads into your browsing sessions.
How Do Proxies and VPNs Affect Online Gaming?
- Proxies: May offer lower latency but do not secure your connection.
- VPNs: Can protect against DDoS attacks but might increase ping times due to encryption overhead.
Conclusion
Choosing between a proxy and a VPN depends on your specific privacy, security, and performance needs. Proxies are suitable for low-risk activities that require basic IP masking and faster speeds. VPNs offer comprehensive security features, including encryption and enhanced anonymity, making them ideal for safeguarding sensitive information and maintaining privacy across all online activities.
Final Recommendations
- For Basic Tasks: Use a proxy to bypass simple restrictions or mask your IP address.
- For Enhanced Security: Opt for a VPN to encrypt your data and protect your privacy.
- For Maximum Anonymity: Consider combining a VPN with the Tor network for layered security.
By understanding each option’s strengths and limitations, you can make an informed decision about which best suits your online privacy and security needs.